First Name
City
State
Email Address
First Name
City
State
Email Address

Sign Up for Our
Informative
Newsletter
Network Security and Training
You need to comply with either internal security policies or government security requirements, and an essential piece of the puzzle is to scan your networks from the outside in, to look for vulnerabilities and configuration problems
Whether we like it or not, if we are connected to the Internet we are all potential targets. There is a very good chance that your network has been recently scanned for vulnerabilities by the bad guys, looking for easy ways to break in. It may be happening right now! You had better be the one who does the most comprehensive scan first, and fixes any holes that cyber criminals might use to penetrate your network. We can help you with that!
There is no such thing as total security, no matter how much money or manpower you throw at the problem it will continue to evolve, therefore,
Your Goal Must Be A Legally Defendable Level of Security.
Vulnerability Scanning and Penetration Testing
Networking Delaware offers a service that scans your network and web-apps from the outside, and uses the same techniques as black hat hackers to find weaknesses in your network or systems. It highlights the vulnerabilities that are exploitable by remote hackers. Our vulnerability scans show the low-hanging fruit that black hats will go after, and what needs to be done to remediate these weaknesses that might result in a compromised website or corporate network. These vulnerability scans are done remotely, and will result in a clear report on what was found and what to do about it. We feature everything you need and nothing you don’t: high-speed discovery, asset profiling, sensitive data discovery, and a ‘business context’ vulnerability analysis of your security posture with the aim to prioritize your highest business risks.
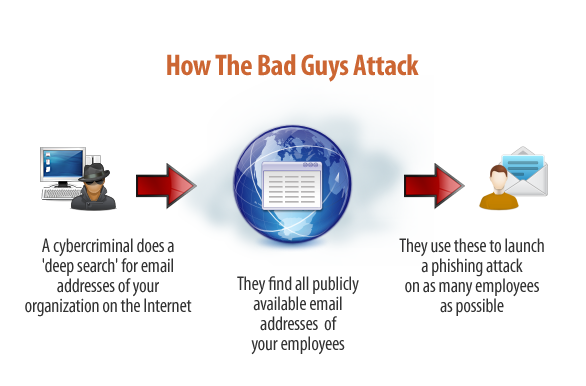
Are you aware that many of the email addresses of your organization are exposed on the Internet and easy for cybercriminals to find ? With these addresses they can launch phishing attacks on your organization. This type of attack is very hard to defend against, unless your users are highly trained in ‘security awareness’.
The bad guys only need to find one email address in your organization to ascertain the email format used for other employees (example John Smith @yourdomain.com could have an email address of j.smith@ or john.smith@ or john_smith@ or some other format. The point is there is a good chance that other employees will have email addresses in the same format.
IT Security specialists call this your ‘phishing attack surface‘. The more of your email addresses that are floating around out there, the bigger your attack footprint is, and the higher the risk is. It’s often a surprise how many addresses are actually out there.
Security is a shared responsibility that requires everyone to participate or risk becoming just another statistic.
Email Exposure Check
Security Awareness Training for Regulatory Compliance
All businesses and organizations are susceptible to "phishing" attacks. In fact almost all of the big expensive data breaches you have read about recently have happened due to "phishing" emails and social engineering; Not hard "hacking" and vulnerability exploits. This proves once again that the human factor is the weakest link in security.
In 2012, between January 1 and November 12, there were 417 data breaches identified in the US alone. It is such a huge problem that government agencies have mandated that certain industries and sectors must provide security awareness training to their employees.
According to DataLossDB, the top five largest breaches in 2013 affected about 450 million records and amazingly, this data was complied before the Target breach.
Various regulations such as GLBA, PCI DSS, HIPAA, and SOX require that Security Awareness Training be performed regularly. Networking Delaware can help you plan and implement your Security Awareness Training Program to ensure a comprehensive and easy-to-deploy training regimen that satisfies your examiner’s expectations.
Some of these sectors and the mandating legislation are:
Any Business Accepting Credit Cards: PCI DSS 2.0
Health Care: HIPPA
Financial Services: Gramm-Leach-Bliley Act (GLBA) Title V - Section 501
Publically Traded Companies: Sarbanes-Oxley Act, Section 404 Based on COBIT ™
Federal Government: Federal Information Security Management Act (FISMA) NIST SP 800
Energy Industry and Infrastructure: FERC Cyber Security Standard CIP-004-1: Personnel & Training
Networking Delaware can provide this very important training using an extremely effective, proven web-based training method that meets the requirements of all these various mandates.. There is no need for your employees to come to our facility or travel to some distant city for the training.
PCI DSS 2.0 Training for Any Business Accepting Credit Cards
Your organization accepts credit cards, so you need to be compliant with the new PCI DSS 2.0 standard. But are you following the rules? Non-compliance could cause you to lose your merchant account. For the first time, there is a simple course that cuts through the confusion and clearly tells you how you become and stay PCI compliant.
This is a high-quality 30 minute, web-based interactive training using real examples of credit card fraud, and how to protect your organization against this by being PCI DSS 2.0 (Payment Card Industry Data Security Standard) compliant. This course is for anyone that’s responsible for handling credit cards in your organization and qualifies as Security Awareness Training. Especially owners, the CFO or Controller, managers and IT people in charge of credit card processing should take this course. After the training, you are able to download essential references regarding being or becoming PCI compliant.
PCI DSS 2.0 2011, the new PCI standard became available at the beginning of 2011, and from Jan 2012 organizations must stop using the previous version, but do you know what the changes are? There are four different levels of merchants, with different compliance rules applying to each. Which level are you? What is a SAQ, (Self Assessment Questionnaire) and which one(s) do you fill out? There are 12 main requirements with over 250 rules, but which rules apply to you? Take the PCI Simplified course now and find out!

©2012 Networking Delaware, LLC
Cybercrime is on the rise and unfortunately so are the costs; the costs of protecting yourself and the larger cost of not protecting yourself adequately.


(302)
368-8630
Networking
Delaware
I.T. Services
